Update (October 1, 2004): It appears that current versions of the software described in this article may actually ask the user for permission before taking action.
What's worse than spyware (software that collects and transmits information about your computer use without your knowledge)? How about configuration management software that is installed on your personal computer without your knowledge and consent? Such software can be used to install spyware, change your configuration, and may even make your computer unusable.
This story starts with the somewhat mysterious files, "tgcmd.exe" and "tgfix.exe". I first became aware of these files when my personal firewall asked me if I wanted to allow them to access the Internet. I searched the web for information about them, but didn't find anything. (I searched again recently and found them mentioned on Practically Networked by someone who seems to know something about them.) Since I had no information about the files, I intermittently allowed and denied access to see what would break.
Following some strange events (some of which are described below), I poked around around in the registry a little and found that the files were from support.com. In the @HOME situation from the Practically Networked page, the support.com software is presumably managed by @HOME. The implication is that among other things, @HOME uses the software to automatically reconfigure systems to use their proxies, even if the user has intentionally disabled the proxies. In my case, support.com's software was included with my Sony laptop, and was presumably managed by Sony (although they may have outsourced it -- eek). Since I removed the software when I determined what it was, I don't know much about how Sony was using it, but it appears that they were actively using it.
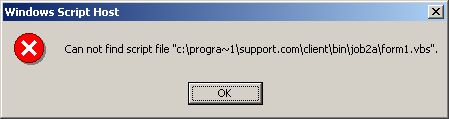
Not long ago I got an error on startup -- failure to execute a .vbs file that didn't exist on my system, but was expected to be under the support.com directory. I didn't delete that file, and I had never gotten that error before, so it seems likely that it was "supposed to" have been created and executed by support.com's software. I guess my intermittent denial of Internet access prevented the file from being obtained, but allowed the system to be instructed to execute it.
In addition to its ability to remotely manage your configuration, it seems that this software can install and execute other software. When I searched the web for name of the missing .vbs file to learn what it might be, the only page that seemed likely to be related was discussing a sample .vbs script provided by Microsoft. (I hope that doesn't mean it was written by an inexperienced person using a sample as a basis. I don't want that kind of stuff being automatically delivered to and executed on my system!)
Sep 17, 2001 Update: In cleaning up my hard drive today, I noticed that
I actually captured the error message:

If the ".vbs" extension sounds familiar, it should -- it's used by many of the recent e-mail worms, including "Love Letter" and "Anna Kournikova". Not all .vbs files are malicious -- in fact, most are legitimate, but if you can create and execute arbitrary .vbs files on a system, you essentially have full control of that system.
![[ALL YOUR CONFIGURATION ARE BELONG TO US !!]](allyourconfig.jpg) The support.com web site has
a list of some
other customers (some of which I assume use it internally to manage their
own corporate computing resources). It seems clear that the package allows the
manager (@HOME, Sony, or whoever) to make configuration changes to the client
system (your system). You can see a brief (but scary)
demo of the software
at support.com's web site. To get a
little perspective, it might help to imagine the thoughts of an underpaid and
frequently abused customer support representative wringing his or her hands
with anticipation while watching the same demo.
The support.com web site has
a list of some
other customers (some of which I assume use it internally to manage their
own corporate computing resources). It seems clear that the package allows the
manager (@HOME, Sony, or whoever) to make configuration changes to the client
system (your system). You can see a brief (but scary)
demo of the software
at support.com's web site. To get a
little perspective, it might help to imagine the thoughts of an underpaid and
frequently abused customer support representative wringing his or her hands
with anticipation while watching the same demo.
I don't have any information about the security of support.com's software, but assuming it's impervious to attack (haha), I am uncomfortable with ongoing full control of my home computer to random employees of a large corporation (I don't know who at Sony was assigned to management of my system) without my explicit knowledge and consent. I'm also uncomfortable with the idea that a large corporation would assume that its customers would be comfortable with such a scheme.
There are some interesting discussions about this in Google's Usenet database (http://groups.google.com). Here are some highlights:
Trademarks are property of their owners (shouldn't that go without saying?).
